In my experience, fixing the issue of Windows Defender virus protection turning off can be frustrating.
July 2025: Enhance your computer’s performance and eliminate errors with this cutting-edge optimization software. Download it at this link
- Click here to download and install the optimization software.
- Initiate a comprehensive system scan.
- Allow the software to automatically fix and repair your system.
Causes and Solutions for Disabling Issues
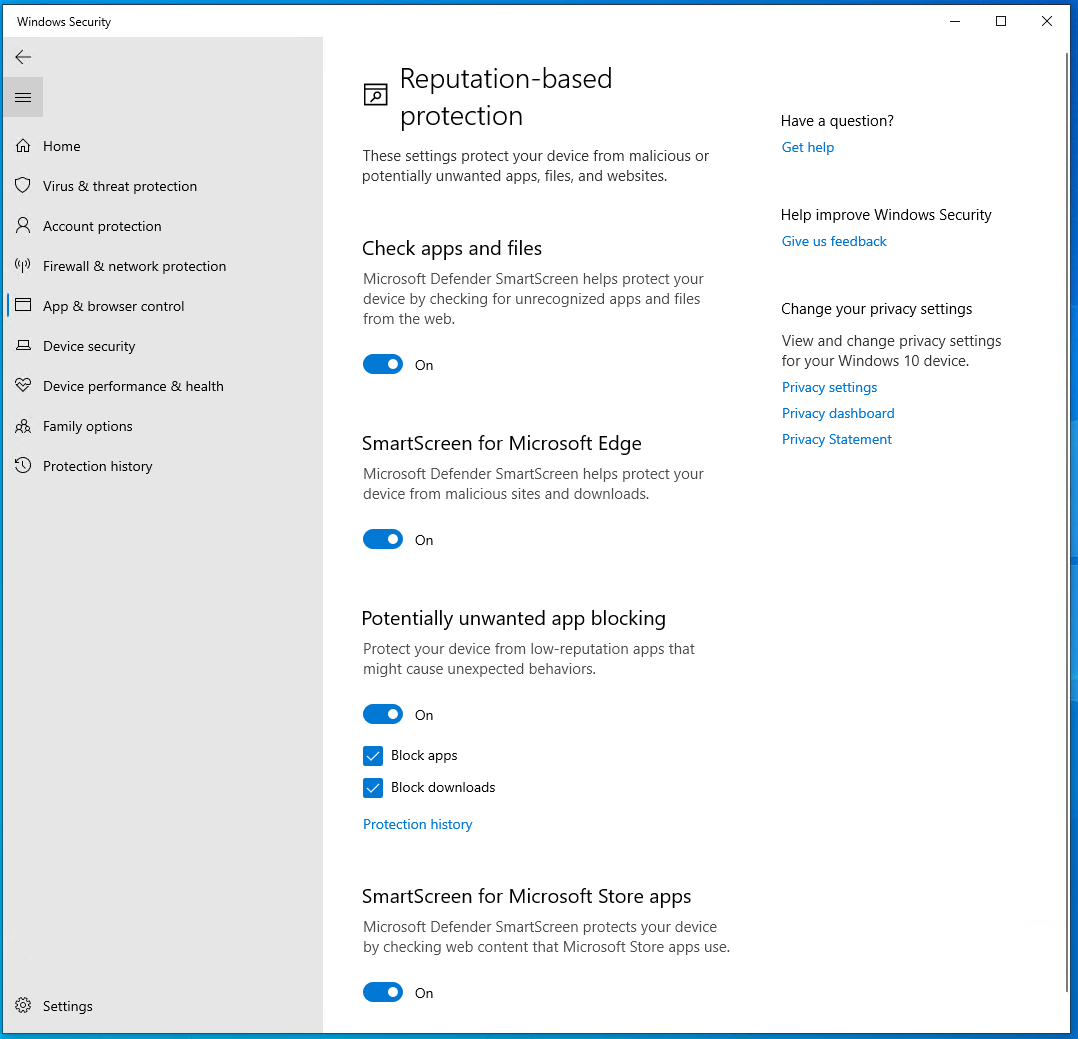
Causes: One of the common causes for Windows Defender virus protection turning off is due to conflicting third-party antivirus software installed on the computer. Additionally, malware infections or corrupt system files can also cause Windows Defender to disable itself.
Solutions: To fix this issue, first ensure that there are no other antivirus programs running on the system. If there are, uninstall them to prevent conflicts with Windows Defender. Next, run a full system scan to check for any malware that may be causing the antivirus to turn off. Additionally, try resetting Windows Defender settings to default by following these steps: Open the Start menu, type “Windows Security,” click on it, then go to “Virus & threat protection,” click on “Manage settings,” and toggle all options to “On.”
Another common solution is to check for Windows updates and install any pending ones. Sometimes, outdated software can cause issues with Windows Defender. By keeping the system up to date, you can ensure that the antivirus program functions properly. If these steps do not resolve the issue, consider running the Windows Defender Offline scan to detect and remove any persistent malware that may be affecting the antivirus program.
It is also recommended to regularly back up important files and data to prevent data loss in case of a malware attack. By creating backups, you can restore your system to a previous state if Windows Defender is unable to protect your files. Additionally, ensure that your system clock is set correctly, as an incorrect date or time can also cause Windows Defender to turn off.
Resetting and Updating Defender
| Problem |
Solution |
| Windows Defender virus protection keeps turning off |
Resetting and updating Defender |
Managing Third-Party Antivirus Software
If you are experiencing issues with Windows Defender virus protection turning off, it may be due to conflicts with third-party antivirus software. Here’s how you can manage third-party antivirus software to ensure Windows Defender stays on:
– **Check for Incompatibility:** Some third-party antivirus software may not work well with Windows Defender. Make sure to check for any known compatibility issues between the two programs.
– **Disable or Uninstall:** If you are using a third-party antivirus software that is causing conflicts with Windows Defender, consider disabling or uninstalling it. This will allow Windows Defender to function properly without any interruptions.
– **Enable Windows Defender:** Once you have disabled or uninstalled the third-party antivirus software, make sure to enable Windows Defender. You can do this by going to the Windows Security app and ensuring that Real-time protection is turned on.
– **Regularly Update:** It’s important to keep both your third-party antivirus software and Windows Defender up to date. This will ensure that you are protected against the latest threats and that both programs work smoothly together.
– **Monitor Performance:** Keep an eye on the performance of both Windows Defender and your third-party antivirus software. If you notice any issues or conflicts, address them promptly to prevent Windows Defender from turning off.
– **Seek Support:** If you are still having trouble managing third-party antivirus software with Windows Defender, consider reaching out to the support teams of both programs for assistance. They may be able to provide you with specific solutions tailored to your situation.
Adjusting Group Policy and Registry Settings
To adjust Group Policy and Registry settings to fix Windows Defender virus protection turning off, follow these steps:
1. Open the Group Policy Editor by pressing Windows Key + R, typing ‘gpedit.msc’ and hitting Enter.
2. Navigate to Computer Configuration > Administrative Templates > Windows Components > Windows Defender Antivirus.
3. Look for the ‘Turn off Windows Defender Antivirus’ policy setting and double click on it.
4. Select ‘Disabled’ and click on ‘Apply’ and then ‘OK’ to save the changes.
5. To adjust Registry settings, press Windows Key + R, type ‘regedit’ and hit Enter.
6. Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender.
7. Look for a DWORD value called ‘DisableAntiSpyware’ and double click on it.
8. Change the value data to ‘0’ and click on ‘OK’ to save the changes.
9. Close the Registry Editor and restart your computer to apply the changes.
Ensuring Ongoing Protection and Data Security
To ensure ongoing protection and data security on your device, it is important to address any issues with Windows Defender virus protection turning off. This can leave your device vulnerable to potential threats and security breaches.
If you are experiencing this issue, one possible solution is to check for any conflicting antivirus software on your device. Sometimes, having multiple antivirus programs installed can cause conflicts and result in Windows Defender turning off. Make sure to uninstall any other antivirus software and keep only Windows Defender running for optimal protection.
Additionally, update your Windows operating system and Windows Defender to the latest version. This can help resolve any bugs or issues that may be causing Windows Defender to turn off unexpectedly. Regular updates are essential for keeping your device secure and protected against the latest threats.
If the issue persists, you can try running a full system scan with Windows Defender to check for any malware or viruses that may be affecting its functionality. Removing any detected threats can help resolve the issue and ensure that Windows Defender stays enabled and provides continuous protection for your device.
It is also important to enable real-time protection and cloud-delivered protection in Windows Defender settings. These features help to detect and block threats in real-time, providing an additional layer of security for your device. Make sure that these settings are turned on to keep your device protected at all times.
In addition to these steps, it is recommended to create regular backups of your important data to prevent data loss in case of a security breach or malware infection. Backing up your files on an external drive or cloud storage can help you recover your data in case of any unexpected issues with Windows Defender or other security measures.
FAQs
Why does my antivirus keep turning off?
Your antivirus may keep turning off due to system updates that need to be installed or conflicts with other third-party antivirus or firewall software on your computer.
Why does Microsoft Defender keep getting turned off?
Microsoft Defender keeps getting turned off because mobile devices have features that save battery life by stopping background apps, which can affect the app’s accessibility permission needed for the web protection feature to run.
Why does Windows Defender keep stopping?
Windows Defender keeps stopping due to corrupted Windows system files. Conducting a SFC scan can help detect and fix these files to resolve the issue.
How do I stop Windows antivirus from turning back on?
To stop Windows antivirus from turning back on, you can navigate to the Computer Configuration settings, locate Microsoft Defender Antivirus, find the option for “Turn off Microsoft Defender Antivirus,” and enable it by checking the box.